本文最后更新于38 天前,其中的信息可能已经过时,如有错误请发送邮件到1416359402@qq.com
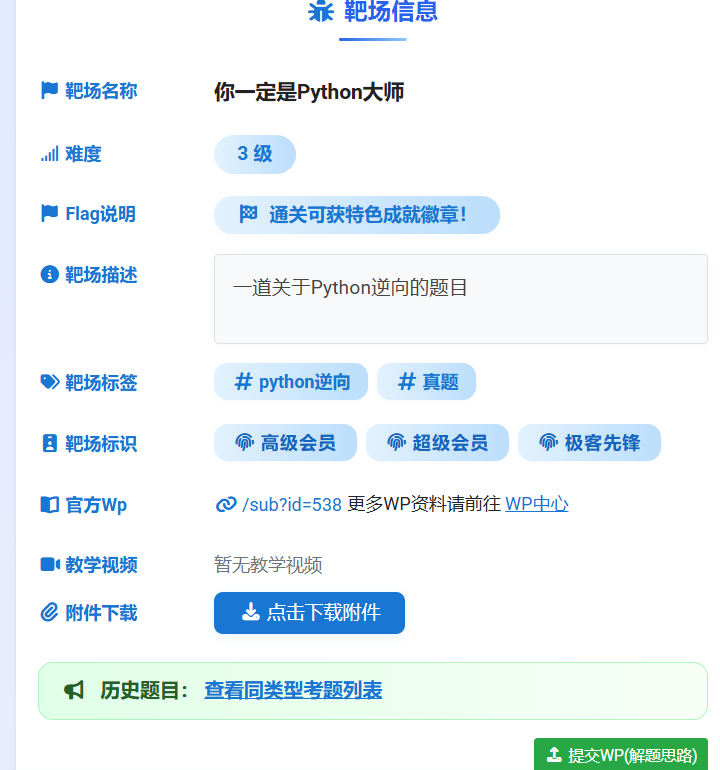
是一个.pyc的文件
下载pip install uncompyle6反编译
D:>uncompyle6 target.pyc
D:pythonLibsite-packagesclickcore.py:1213: UserWarning: The parameter --version is used more than once. Remove its duplicate as parameters should be unique.
parser = self.make_parser(ctx)
D:pythonLibsite-packagesclickcore.py:1206: UserWarning: The parameter --version is used more than once. Remove its duplicate as parameters should be unique.
self.parse_args(ctx, args)
# uncompyle6 version 3.9.2
# Python bytecode version base 3.8.0 (3413)
# Decompiled from: Python 3.12.0 (tags/v3.12.0:0fb18b0, Oct 2 2023, 13:03:39) [MSC v.1935 64 bit (AMD64)]
# Embedded file name: 太好了是python糕手我们有救了.py
# Compiled at: 2025-10-04 20:43:26
# Size of source mod 2**32: 1347 bytes
cipher = [
48, 55, 57, 50, 53, 55, 53, 50, 52, 50, 48, 55, 101, 52, 53, 50,
52, 50, 52, 50, 48, 55, 53, 55, 55, 55, 50, 54, 53, 55, 54, 55,
55, 55, 53, 54, 98, 55, 97, 54, 50, 53, 56, 52, 50, 52, 99, 54,
50, 50, 52, 50, 50, 54]
def str_to_hex_bytes(s: str) -> bytes:
return s.encode("utf-8")
def enc(data: bytes, key: int) -> bytes:
return bytes([b ^ key for b in data])
def en3(b: int) -> int:
return b << 4 & 240 | b >> 4 & 15
def en33(data: bytes, n: int) -> bytes:
"""整体 bitstream 循环左移 n 位"""
bit_len = len(data) * 8
n = n % bit_len
val = int.from_bytes(data, "big")
val = (val << n | val >> bit_len - n) & (1 << bit_len) - 1
return val.to_bytes(len(data), "big")
if __name__ == "__main__":
flag = ""
data = str_to_hex_bytes(flag)
data = enc(data, 17)
data = bytes([en3(b) for b in data])
data = data[None[None:-1]]
data = en33(data, 32)
if data.hex() == cipher:
print("Correct! ")
else:
print("Wrong!!!!!!!!")
# okay decompiling target.pyc
这个代码加密过程
1.将flag字符串转换为字节序列(UTF-8编码)
2.对每个字节与17进行异或
3.对每个字节进行高低4位交换(en3函数)
4.对整个字节序列进行切片操作:data[None[None:-1]],这个写法看起来有问题,实际上可能是反编译的错误。根据上下文,这个切片操作可能是反转字节序列,即data[::-1]。
5.对整个字节序列进行循环左移32位(en33函数)加密步骤的逆序:
- 整体bitstream循环右移32位(de33函数)
- 反转字节顺序(再次反转)
- 对每个字节进行高低4位交换(与en3相同,因为交换两次等于本身)
- 对每个字节与17进行异或(与加密相同,因为异或两次等于本身)
- 将字节解码为字符串
py3解密代码:
cipher = [
48, 55, 57, 50, 53, 55, 53, 50, 52, 50, 48, 55, 101, 52, 53, 50,
52, 50, 52, 50, 48, 55, 53, 55, 55, 55, 50, 54, 53, 55, 54, 55,
55, 55, 53, 54, 98, 55, 97, 54, 50, 53, 56, 52, 50, 52, 99, 54,
50, 50, 52, 50, 50, 54
]
def de3(b: int) -> int:
"""en3 的逆操作 - 高低4位交换"""
return b << 4 & 240 | b >> 4 & 15
def de33(data: bytes, n: int) -> bytes:
"""en33 的逆操作 - 整体 bitstream 循环右移 n 位"""
bit_len = len(data) * 8
n = n % bit_len
val = int.from_bytes(data, "big")
val = (val >> n | val << bit_len - n) & ((1 << bit_len) - 1)
return val.to_bytes(len(data), "big")
def decrypt():
# 将 cipher 列表转换为字节
# cipher 实际上是十六进制字符串的 ASCII 码值
hex_str = ''.join(chr(x) for x in cipher)
print(f"Hex string: {hex_str}")
# 将十六进制字符串转换为字节
data = bytes.fromhex(hex_str)
print(f"原始数据: {data.hex()}")
# 解密步骤(与加密相反的顺序):
# 1. 循环右移32位(加密是左移)
data = de33(data, 32)
print(f"循环右移后: {data.hex()}")
# 2. 反转字节顺序(加密是反转)
data = data[::-1]
print(f"反转后: {data.hex()}")
# 3. 高低4位交换(与加密相同,因为交换两次等于原值)
data = bytes([de3(b) for b in data])
print(f"高低位交换后: {data.hex()}")
# 4. 异或17(与加密相同,因为异或两次等于原值)
data = bytes([b ^ 17 for b in data])
print(f"异或解密后: {data.hex()}")
# 尝试解码
try:
flag = data.decode('utf-8')
return flag
except UnicodeDecodeError:
# 如果UTF-8解码失败,尝试其他编码或直接显示字节
print(f"解码失败,原始字节: {data}")
return None
# 执行解密
if __name__ == "__main__":
flag = decrypt()
if flag:
print(f"nFlag: {flag}")
else:
print("解密成功但无法解码为有效字符串")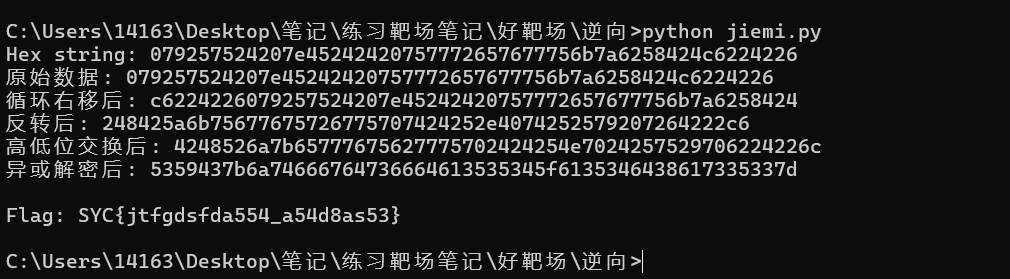
SYC{jtfgdsfda554_a54d8as53}